
Identity Protection Built Around You.
Guided by AI, brought to life by innovative people.
Protect your family and digital life from scams, cyber threats, and identity theft with our industry-leading security solution. Live stress-free, knowing you're safe online and offline.

























Online Crime Is Surging
As life moves online, criminals find new ways to steal — often unnoticed until your finances, credit, and even your reputation suffer. Protecting your identity and devices has never been more essential.

was lost due to identity theft and fraud last year.
of identity theft victims had difficulty covering the cost of basic needs.
cases of fraud and identity theft reported last year.
of Americans have already experienced identity theft.
Think of Us As Your Radar, Defender, and Advocate, All in One.











What Fuels Our Features
At IdentityIQ, it’s not just about features — it’s about people. Our team works with purpose and care to deliver smart solutions that make your life easier. Because we've got your back, you can focus on what really matters while knowing that we are handling the hard stuff.
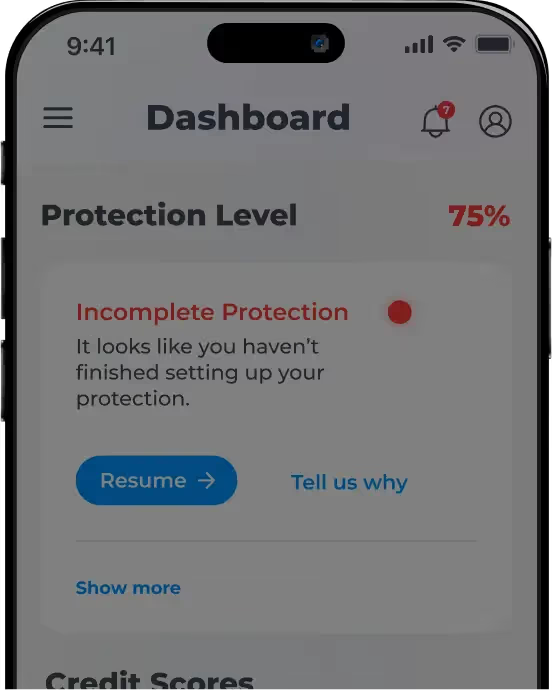
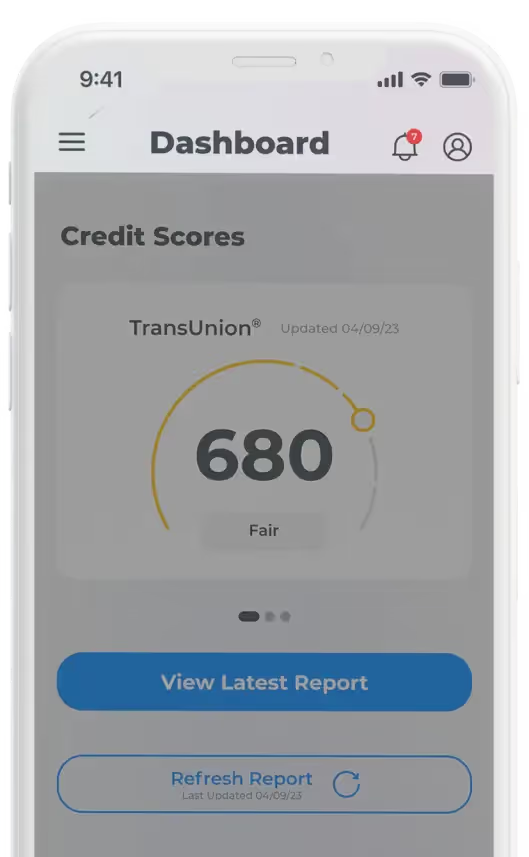
Protection at Your Fingertips
Review alerts, access your data, and track your financial progress — all from your personalized dashboard.




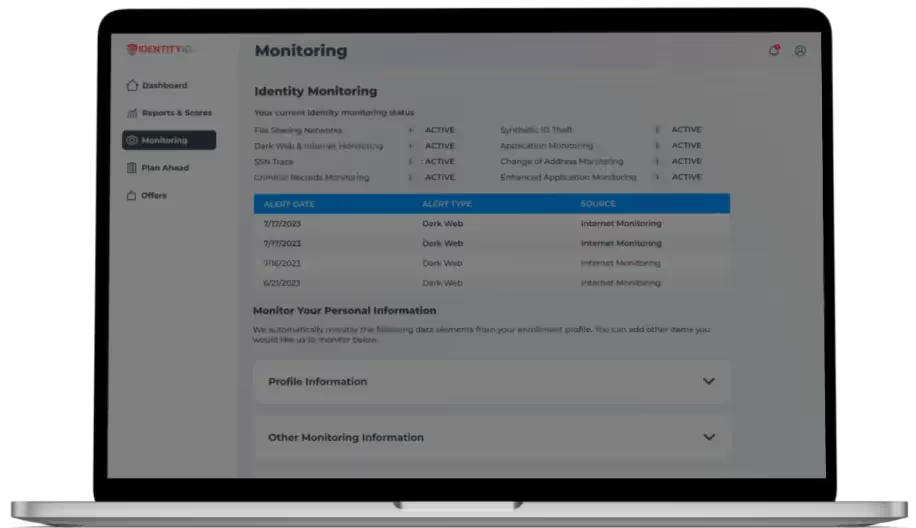
We Monitor So You Don’t Have To
IdentityIQ is your 24/7 security powerhouse, using everything from cutting-edge AI and law enforcement partnerships locally, nationally and globally to scan the digital world for threats. We monitor billions of transactions every second across 250,000+ databases in 25 languages — detecting threats before they strike. From credit alerts to dark web monitoring, we've got you covered.

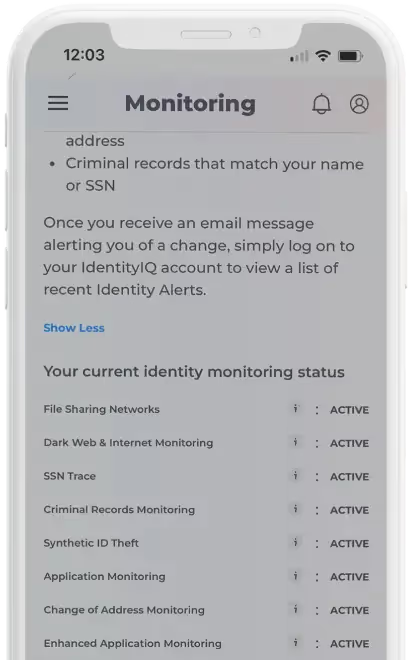


Application Monitoring
Criminals frequently use stolen information to open unauthorized accounts, such as utilities, payday loans, or credit cards. Our monitoring system scans extensive networks, including financial institutions, utility providers, and non-credit inquiries, to detect fraudulent applications linked to your personal data. Even if a credit check isn’t performed, we can identify attempts to use your information — whether it’s your name, Social Security number, or other sensitive data. When possible suspicious activity is detected, we alert you, so you can take swift, decisive action to help prevent and stop fraud.




Social Security Number Monitoring
IdentityIQ delivers unparalleled Social Security number (SSN) monitoring to protect one of your most critical identifiers — and it doesn’t stop with you. With our family plan, you can also monitor your children’s SSNs, safeguarding their identities from misuse. Our advanced system scans a vast network of databases for possible suspicious activity involving your SSN or your child’s, from financial accounts to utility services. Unlike standard services that only flag mismatched names or addresses, we alert you to activity tied to these sensitive identifiers. This comprehensive, real-time protection helps make sure you and your family stay ahead of potential threats.




Dark Web Monitoring
We search the darkest corners of the internet — hidden marketplaces, forums, and chat rooms — where stolen personal information is bought and sold. Combining cutting-edge AI with the expertise of former FBI agents, law enforcement professionals, and white hat hackers, we proactively monitor for your data in real-time. Whether it’s your Social Security number, credit card details, or email address, our system continuously tracks and detects threats as they emerge. The moment your information is found, we send you an alert, giving you the chance to act immediately and prevent criminals from exploiting your stolen or leaked data.



Change of Address Monitoring
IdentityIQ comprehensive monitoring goes beyond traditional credit bureaus. We track more than 180,000 data furnishers, including all three major credit bureaus, the National Change of Address registry, and the USPS system, to catch address changes and other critical data updates. Unlike standard credit bureau monitoring, which often overlooks critical address updates, our advanced system alerts you to possible suspicious activity, even if it doesn't involve your credit.


Financial Accounts Monitoring
IdentityIQ financial accounts monitoring goes beyond traditional bank security measures. We employ advanced AI algorithms to analyze transaction data, identifying patterns that may indicate fraudulent activity. By monitoring your accounts in real-time, we can detect anomalies such as unusual spending patterns, unauthorized charges, or transactions from unfamiliar locations. Our system can also flag potential data breaches at retailers, alerting you to potential risks before they impact your finances.




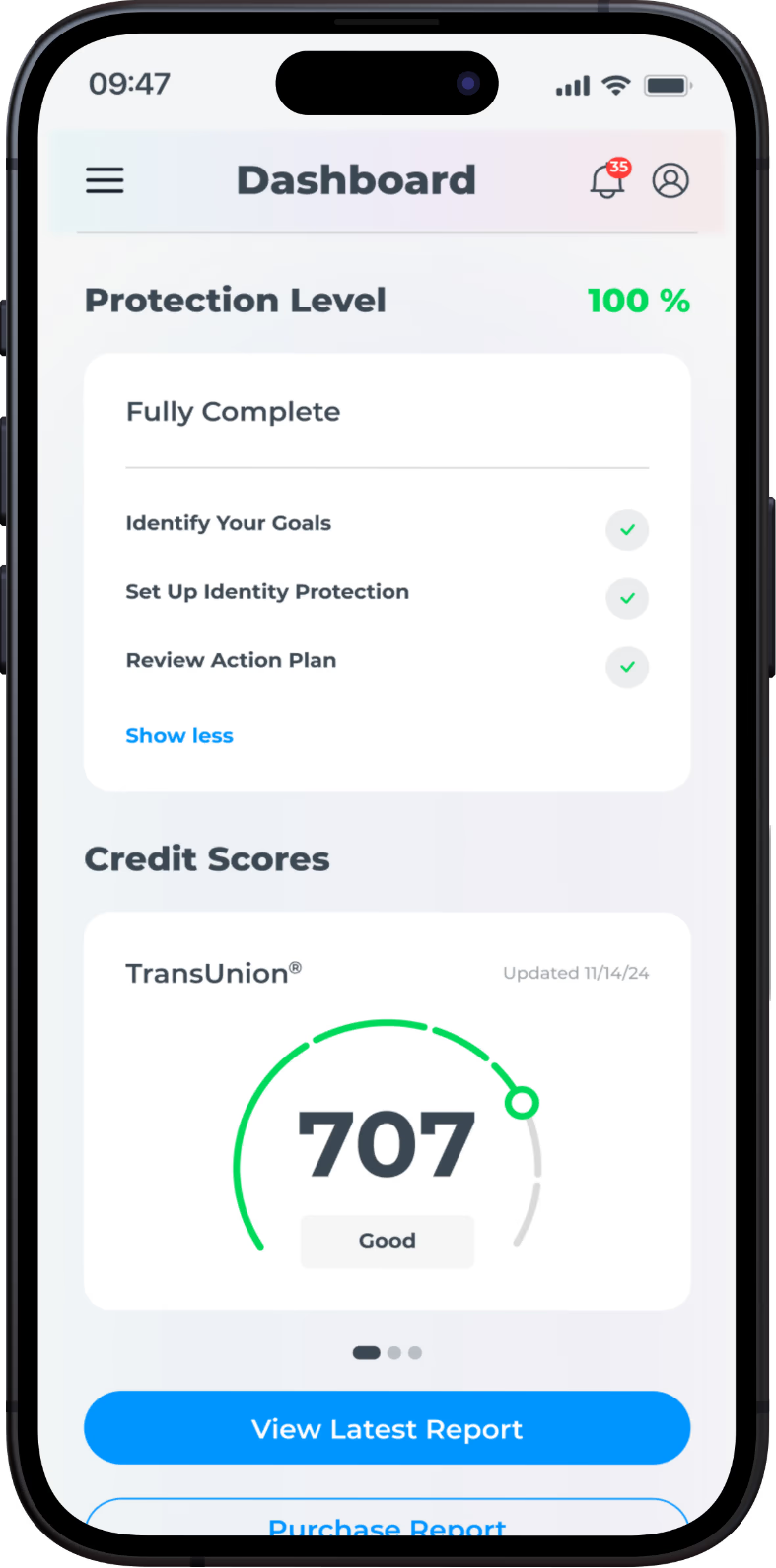
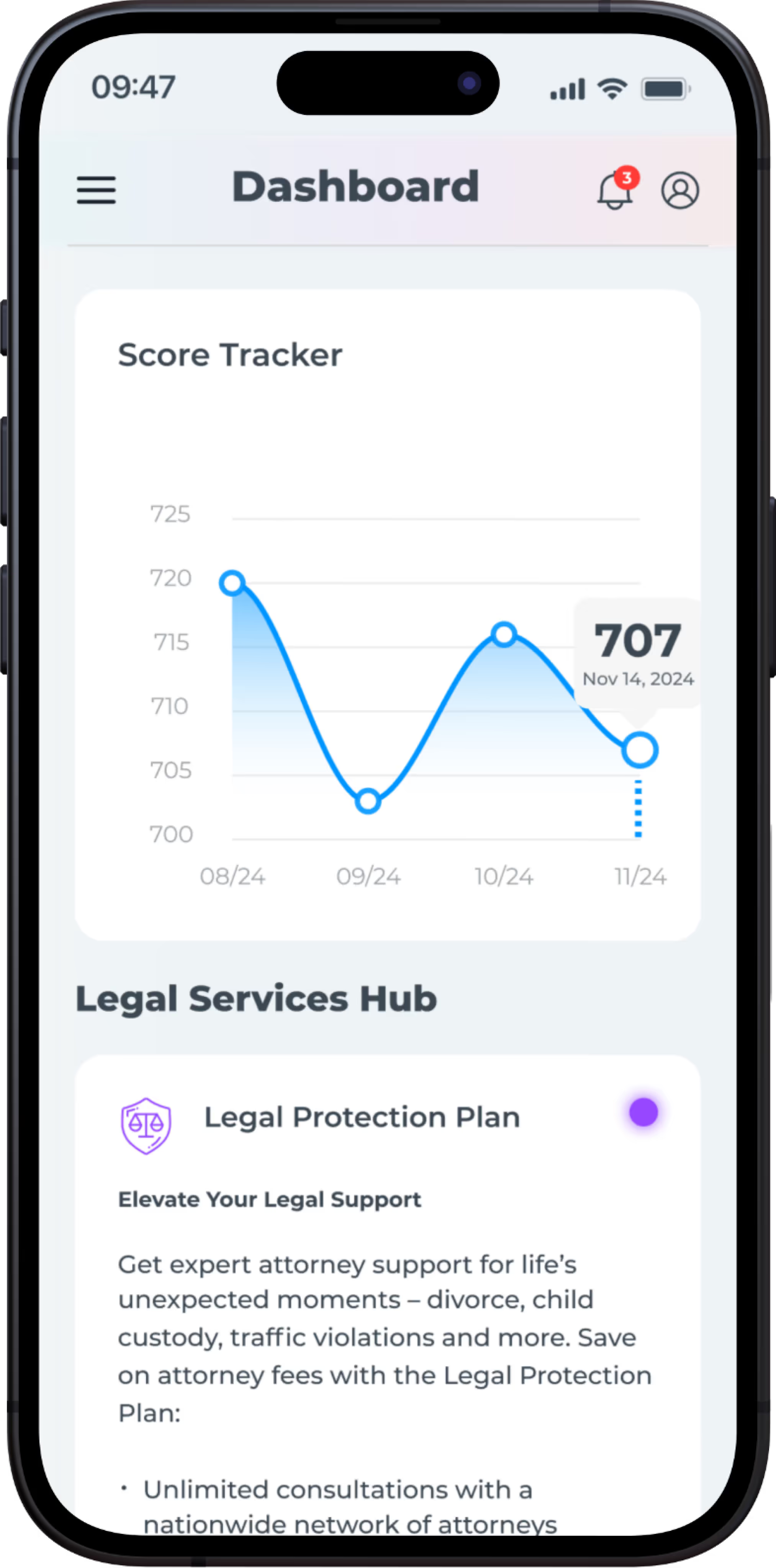
Credit Monitoring
Leveraging our 50+ years of experience and direct relationships with major credit bureaus, IdentityIQ Enhanced Credit Monitoring provides a comprehensive overview of your credit health. We go beyond traditional credit monitoring, alerting you to critical changes, such as the addition of authorized users, significant fluctuations in your credit score, and updates to your credit accounts. By monitoring these key indicators, we empower you to detect potential fraud or unauthorized activity early on, safeguarding your financial future.
IdentityIQ: Personalized Protection for Your Lifestyle
Your identity is extremely valuable and deserves protection. Pick a plan that meets your safety needs and your budget.
4 Million People Just Like You Trust Us with Their Identity





















